Current location, banking information, personal information… there are no limits to what a breach in mobile security can give hackers access to.
In a Verizon Mobile Security Index report, it was found that mobile threats were escalating: Around 83% of the organizations surveyed reported they were at risk from mobile threats; 86% said mobile threats are growing more quickly than other threats; almost 50% said they sacrificed mobile security for business objectives and as a result, were 2x more likely to be compromised.
Mobile apps are vulnerable to attack from various points. Here are some of the major sources of threats, and possible solutions for you to consider.
The cloud environment
When it comes to transmission of data, there are security risks between the pathways and endpoints, which hackers can exploit.
Areas of concern for mobile application security include authorization, authentication and session handling. Secure authentication can be an issue for mobile apps as longer passwords are more difficult to deal with on smaller devices. Additionally, if some applications reuse tokens for re-authentication purposes, it leaves the app open to hackers to access the tokens and imitate a valid user.
Small changes anywhere in the system, including in the dependencies, can have a major impact, especially on security. Often, something as simple as forgetting to fix an access issue could result in later exploitation. In mobile apps, several modular elements are linked via APIs and microservice calls, which means that a single security flaw could have a domino-like effect throughout the app.
The solution would be to use an automated tool with a comprehensive database to keep an eye on vulnerabilities in open source components.
Speed of deployment
Cloud environments are constantly changing. The rapid software release cycles mean that any component of the microservices application can be updated every day. Infrastructure as Code (IaC) and immutability means that apps are constantly torn down and recreated.
The solution would be to make security an integral part of the app lifecycle. One way would be to update your process from DevOps to DevSecOps. Also, consider planning security check through the application development lifecycle, and not just during launch.
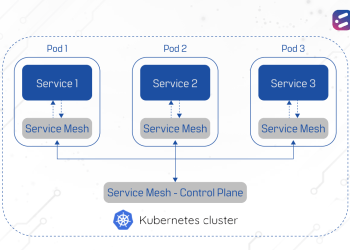
Serverless structure
Cloud-native apps are based on containerization, microservices architecture, dynamic orchestration, and serverless platforms, and therefore their entire lifecycle is often solely in the cloud environment. While on the one hand, this ensures scalability, resilience, and quick development and deployment, on the other, it raises security concerns.
When the system is split into multiple callable components with event-driven triggers from different sources, it becomes a target for malicious activity. Serverless computing brings with it its own set of security challenges, like “injection flaws” for instance, where untrusted input is passed directly to an interpreter and gets executed or evaluated.
The solution lies in applying robust authentication schemes, which provide proper access control and protection to every relevant function, event type, and trigger. Security best practices for orchestrators like Kubernetes include isolating nodes, limiting and monitoring traffic between containers, and using third-party authentication for the API server.
Multiple interactions
When there are too many people and systems accessing cloud-native resources, it can lead to security breaches. Providing any entity with greater access than it requires can give rise to more points of security failure.
In this case, the solution lies in assigning unique access and permissions to each container and individual; defining granular permissions for containers in a cluster; and creating a minimal set of permissions for each function or container.
When it comes to mobile application security, quality comes first. And that means quality engineering – it is far better to build security into an application than trying to firefight after development. If you are looking for a solution to your mobile app security challenges, CloudNow has a range of services to offer – talk to us today.